About Us

Who are we?
Predator Stoppers is a nonprofit organization led by “white hat” hackers and other cybersecurity and technology experts with the sole purpose of protecting children online. Using online investigative tactics and techniques, PS hunts down pedophiles, sexual predators, and human traffickers in order to provide critical evidence to US and international law enforcement agencies.

How do we do it?
The Predator Identification Team (PIT) for Predator Stoppers utilizes a multitude of security and intelligence tactics to identify CSAM and “anonymous” child predators in order to supply law enforcement agencies with information that can be used against perpetrators. Most of the cases that are finalized and sent to law enforcement agencies contain actionable, incriminating evidence that can be immediately used by legal prosecutors.

Why do we do it?
As society embraces a hyper digital age, we find it increasingly important to counter the predators that attempt to exploit children online. Strangers have never had easier access to children than they do today, and the digital world that we all enjoy is far closer to the real world than most people realize. There is no greater goal than protecting the innocent.
What We Do

Prevent CSAM Distribution
One of the main priorities of Predator Stoppers is countering the spread of Child Sexual Abuse Material, otherwise known as CSAM. For most people this is known as “child pornography.” Unfortunately, this sort of content is very accessible on today’s social media platforms. Often times, traders of this material create collections that includes thousands of files in order to use it as a source of income by supplying the other predators that seek out this content. We work with some of the top platforms that are used by these predators, such as Snapchat, Discord, Dropbox, and MEGA in order to have these repositories destroyed, and their creators reported.

Targeted Predator Identification (TPI)
Targeted Predator Identification (TPI) is the secondary goal that is primarily performed by our Predator Identification Team (PIT). To achieve this, our investigators work to deanonymize online child predators that are actively grooming young people in their home state or country. This is done by forming strong relationships with law enforcement agencies and collaborating with the necessary teams in order to target local predators that have been deemed active and a danger to society. Our PIT utilizes a variety of intelligence techniques in order to collect incriminating evidence that can be used for legal prosecution.
Data Retention Policy
Regarding data collected on individuals during investigations:
Predator Stoppers collects extensive personal information on individuals involved in active cases. This includes, but is not limited to:
- The submitter of the report
- The victim(s)
- Relatives of the victim(s)
- The predator(s)
- Potential associates of the predator(s)

This information may include: full name, date of birth, phone number, address, place of work, license plate number, IP address, social media accounts, chat logs, information connecting an individual to an online account (or vice versa), online history/digital footprint, chat logs, and anything else that Predator Stoppers deems relevant for tracking an individual in support of a case.
All data is collected using legal processes. Under no circumstance should an individual contact Predator Stoppers with the intention of remaining anonymous. Cases are taken very seriously and have the potential to ruin lives if they are based on a false report. While our practices may seem intrusive to the general public, most of our data is considered public information.
The specific details of information collected will not be disclosed with any individuals that are/were part of a case. Information is only shared with relevant investigation teams or law enforcement.
Predator Stoppers retains information on closed cases for an undisclosed amount of time and reserves the right to hold this data indefinitely.
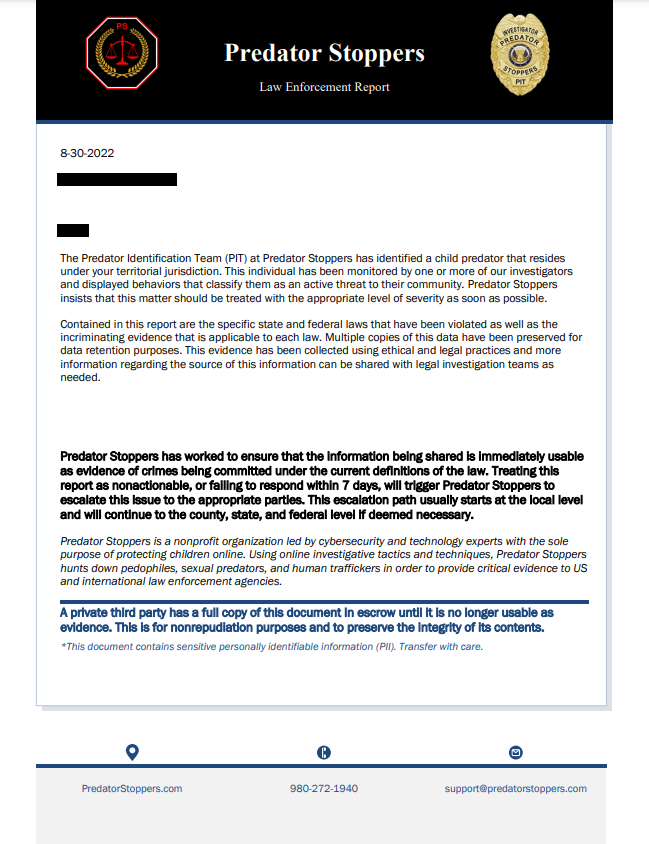
Law Enforcement Collaboration Policy
Engagement Process
Law enforcement offices will receive a detailed report that looks similar to the example provided when being engaged by Predator Stoppers. One of our primary investigators will be assigned to the case and will be the point of contact for any external teams and individuals. All communication will be logged. Contained in the report will be extensive documentation surrounding the case, including but not limited to: personal information on the individual, context of the case, all data collected on the individual, relevant chat logs, audio/video recordings, a list laws being violated, the evidence pertaining to each law, and information on any individual connected to the case. The information found in our report should be considered immediately actionable evidence of serious crimes being committed and addressed urgently.
Escalation Process
Predator Stoppers is proud to fully cooperate with city, county, state, and federal law enforcement agencies, as well as international law enforcement agencies. However, in the event that a law enforcement office is uncooperative, such as a report not getting the attention that it requires, Predator Stoppers will escalate the issue in order for it to gain visibility. Most of the cases that we submit to law enforcement agencies are given the highest severity rating by our internal teams because the individual being reported has been classified an active threat that can cause harm to their community at any time. Because of this, negligence will not be tolerated. Predator Stoppers will escalate the issue by any means necessary to ensure it receives adequate attention and will engage any of our partners, affiliates, and connections in order to address this problem until the resolution of a case is reached, no matter the end-decision. We appreciate your understanding and cooperation.
